- The TCP/UDP ports that are needed in order to run the system
- Types of deployment and associated security
1. TCP/UDP ports needed
The diagram below lists all the TCP/UDP needed at both the server-side and user-side in order to use the R-HUB system. In most cases, you have no control over the user-side ports but you have control over the server-side ports.
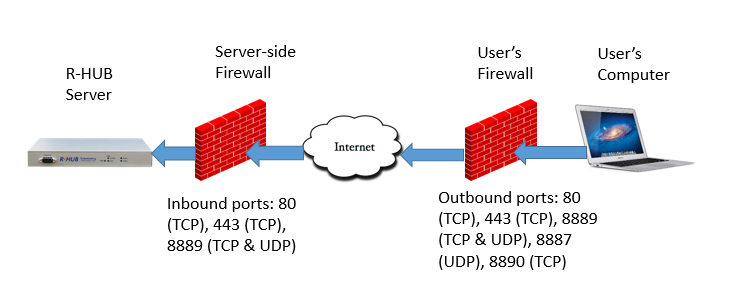
- Configure the server-side ports. Unless you use the internal deployment (see Section 2.1), you need to go to your firewall and do port forwarding in order to forward the incoming traffic on the port 80 (TCP), 443 (TCP) and 8889 (TCP & UDP) to the R-HUB server.
- Configure user-side ports. In most cases, it is impossible to do it since you have no control of users' firewall and you even do not know who they are. Most of users are attendees and they can come from anywhere over the Internet. Fortunately, the outbound traffic is usally harmless and most organizations keep them open. So you do not need to do anything. Also, the most advanced R-HUB firewall traversal technology will keep the system running flawlessly (with reduced functions) even after most of the neeed ports are closed. The least requirement from attendee users is whether they can browse the Internet. If they can, they will be able to join your sessions using the R-HUB system thanks to the R-HUB patented firewall traversal technology.
2. Deployment Types
There are three ways to deploy the R-HUB server:
- Internal deployment: the most secure deployment
- Internal and external deployment: the deployment of R-HUB servers in offices
- External deployment: the deployment of R-HUB servers in data centers or public clouds such as AWS
2.1 Internal Deployment
You place the R-HUB server inside your local network and do not allow access to the server from any user outside your firewall. This is the most secured deployment. It is recommended for secured internal collaboration. If your local network is simple, you do not need to configure anything on your firewall.
1.2 Internal and External Deployment
This is the deployment of the R-HUB servers in offices. It allows internal and external users to join the same sessions. Meanwhile, it allows the host to specify whether a session allows external attendees or not (see the FAQ for details). In order to make the server accessible from both sides of the firewall, you need to go to your firewall and do port forwarding in order to forward the incoming traffic on the port 80 (TCP), 443 (TCP) and 8889 (TCP & UDP) to the R-HUB server. If your firewall has a DMZ function, it is recommended to place the R-HUB server in DMZ.

1.3 External Deployment
This is the deployment of R-HUB servers in data centers or public clounds such as AWS. Although the deployment looks like the services by a third-party service provider, it has fundmental differences in terms of security. With the R-HUB server, you have complete control of the services, and the history and future data. You can tell the server the IPs where you trusted attendees can join your internal sessions (see the FAQ for details).







